· Dayo Adetoye (PhD, C|CISO) · Managing Uncertainty and Complexity · 10 min read
Unlocking Strategic Insights:
Elevating Business Decisions with Advanced Risk Modeling
Is your business ready to tackle today's complex risk landscape? Advanced risk modeling transforms decision-making by predicting cyber threats, optimizing controls, and measuring effectiveness. Discover how to communicate risks, prioritize resources, and drive sustained success with strategic tiered-risk models.

Decision-Making with Tiered Risk Analysis
Our goal is not only to communicate risk to the business to support decision-making to allocate resources to sustain the business’ risk appetite, but we must also make operational and tactical decisions on the selection and deployment of controls as well as the measurement of the efficacy of those controls in helping to manage the aforementioned risk. How do we begin to have that conversation at the appropriate level across the business, while also communicating nuances about inherent uncertainties involved in the risk analysis?
In the first instance we need to adopt a quantitative risk assessment (QRA) methodology. See why here. An effective QRA must both support rational decision-making and communicate the uncertainties involved so that the decision maker can make an informed decision about the assumptions and the model behind the risk estimates.
Strategic Risk Questions
Risk perception and decision-making vary across organizational levels. Executive leadership and board members typically focus on different concerns than operational teams, resulting in distinct decision-making needs. An effective Quantitative Risk Assessment (QRA) should support decisions at all levels, providing clear line-of-sight across the organizational hierarchy.
To illustrate, consider these strategic questions that a robust QRA model can help address:
- What are the chances that the business will not be able to achieve its growth target due to material cybersecurity events?
- What are the top three most consequential cyber threat scenarios facing the business, and what is the likelihood that the expected loss will exceed X million dollars?
- What control deployment architecture gives us the best risk reduction outcomes?
- What metrics and key risk indicators are contributing to the bulk of our risk exposure?
We can categorize these questions into broad tiers, for example:
Tiered Risk Questions
- Tier 0 Risk (T0): Questions about probable futures and forecasting of material risk impact on corporate objectives.
- Tier 1 Risk (T1): Impact Scenario risk questions, such as what classes of risk are most consequential to the business?
- Tier 2 Risk (T2): Assets and controls-focused risk, including the concept of attack paths, controls and their efficacy, attack simulation outcomes etc.
- Tier 3 Risk (T3): Key risk indicators (KRIs) and metrics, feeding T2 risks such as threat/vulnerability arrival rates, burndown rates, survival rates etc.
The risk questions in Tier 0 and Tier 1 are strategic in nature, having to do with executive/board-level decision making, whereas Tier 2 and Tier 3 drive operational and tactical decision making with business units, the security team, IT, engineering, DevOps and so on.
Let us now step through each risk tier, and discuss how you might structure the analysis of risk at each tier.
Tier 3 Risk Analysis: Data-Driven Foundations
Tier 3 risk analysis focuses on metrics and key risk indicators (KRIs) that drive cyber risk. These KRIs provide insight into the susceptibility of systems to material risk events by measuring various factors such as:
- Arrival rates of new vulnerabilities
- Escape rates of undetected vulnerabilities
- Survival rates of known vulnerabilities
- Time-to-live for vulnerabilities
- Burndown rates of remediation efforts
The primary goals of capturing Tier 3 metrics and indicators are:
- To gain situational awareness of fundamental risk drivers
- To understand the causal factors behind cyber risks
- To reduce uncertainty about our actual attack surface and tactical risk exposure (see Decision Making Under Uncertainty)
- To inform intervention decisions that can improve risk outcomes
By modifying behaviors and processes based on these insights, your organization can reduce your systems’ susceptibility to threats. Furthermore, the data collected at this level serves as leading indicators, offering predictive capabilities for potential material events. For instance, shorter time-to-live and survival rates of exploitable vulnerabilities in Internet-facing infrastructure correlate with a lower likelihood of successful exploitation by threat actors.
Tier 3 Risk Analysis: The Foundation of Data-Driven Cybersecurity
Tier 3 Risk Analysis focuses on measuring and tracking key risk indicators (KRIs) and metrics that drive cybersecurity risk. Its primary goal is to provide situational awareness of fundamental risk drivers and it offers predictive insights that helps tilt the balance towards better risk outcomes enabling your organization to make informed decisions and tactical interventions.
For Tier 3 analysis to be effective, you should consider:
- The scope of data collection
- The coverage across systems and networks
- The cadence of metric and KRI collection
By improving the underlying tactical processes of gathering, measuring, and analyzing these KRIs and metrics, you can drive better risk outcomes that positively impact the overall strategic risk posture of your organization.
Tier 3 Risk Analysis in action
For a deeper discussion on the application of Tier 3 risk metrics and KRIs, see Foundational Metrics and Key Risk Indicators.
Tier 2 Risk Analysis: Assets and Controls
Tier 2 Risk analysis elevates the tactical risk metrics of Tier 3, to operational and architectural factors of your risk exposure. For example, what are the attack paths to your critical assets and what controls do you have in place to mitigate the likelihood of a threat actor coming in contact with and abusing those assets?
Tier 2 Risk Analysis: Mapping Attack Paths and Fortifying Critical Assets
Tier 2 Risk Analysis bridges the gap between tactical metrics and strategic risk management by focusing on operational and architectural factors of risk exposure. It elevates the granular data from Tier 3 to provide a comprehensive view of an organization’s cybersecurity posture, emphasizing critical assets and potential attack vectors. Tier 2 also decomposes the mechanics of how the impact scenario risks (Tier 1) materialize.
The following are the key goals of Tier 2 risk analysis:
- Identify and prioritize critical business assets vulnerable to breaches or disruptions
- Map out potential attack paths that threat actors could exploit to access these assets
- Assess the effectiveness of controls in mitigating identified risks
- Understand and ensure the sufficiency, coverage and validation of security control are within our appetite for risk.
Tier 2 Risk Analysis in action
For a deeper discussion on the application of Tier 2 analysis, see The Great Security Bluff: Why Your Controls Might Fail When You Need Them Most.
The analyses of Tier 2 risks are operational and architectural in nature, involving the following key considerations:
- Critical Asset Identification: What are the most vital assets to the business from a breach or disruption perspective?
- Attack Path Analysis: What are the most likely routes a threat actor could take to access critical assets?
- Control Efficacy:
- What controls are in place to reduce the likelihood of threat actors accessing or abusing critical assets?
- How effective are these controls in mitigating cyber threats?
- Control Assurance:
- What is the scope and coverage of our security controls?
- What is the validation cadence to ensure controls are functioning as intended?
- Risk Mitigation Strategies: Based on the analysis of attack paths and control efficacy, what additional measures or improvements are needed to enhance overall security posture?
Modeling and reasoning about control efficacy is discussed in The Great Security Bluff: Why Your Controls Might Fail When You Need Them Most.
Tier 1 Risk Analysis: Impact Scenario
Tier 1 risk analysis provides a predictive analysis of impact scenarios tailored to your company’s vertical and size, enabling strategic-level decision-making for cyber risk management.
Tier 1 risks, also known as Impact Scenario risks, are classes of cyber threats that can have material impacts on a business. These include:
- Ransomware and extortion risks
- Infrastructure compromise
- Business disruption
- Insider threats
- Supply chain disruptions
- Financial fraud
- Intellectual property theft
- etc.
Tier 1 Risk Analysis: Understanding Strategic-Level Cyber Threats
The primary objectives of Tier 1 risk analysis are:
- To understand the likelihood of these risks materializing
- To estimate potential losses when these events occur
- To model probable impacts of thematic risk categories
- To calculate the return on investment of your controls
- Calculate and justify investment in control portfolio initiatives
- To understand the most likely course of attacks to your critical assets
Your methodology should include the following:
- Leverage Tier 2 risk data to inform Tier 1 risk modeling and analysis
- Utilize Monte Carlo simulations based on critical assets, attack paths, and control architecture to estimate likelihood and magnitude of various risk scenarios
- Present results using Loss Exceedance Curves
- Use the simulations to understand the dampening effect of your controls architecture on risks, and the return on investment of your security controls.
Additional Considerations:
- Incorporate cyber loss data (e.g., from Advisen)
- Analyze cyber insurance claims data
- Conduct firmographic comparative analyses of probable loss magnitude and frequencies (e.g., Cyentia Institute’s studies)
Tier 1 Risk Analysis in action
For a deeper discussion on the application of Tier 1 risk analysis for the justification of return on investment of your security controls see the article on ROI Analysis of Control Portfolios.
Tier 0 Risk Analysis: Probable Futures Risk
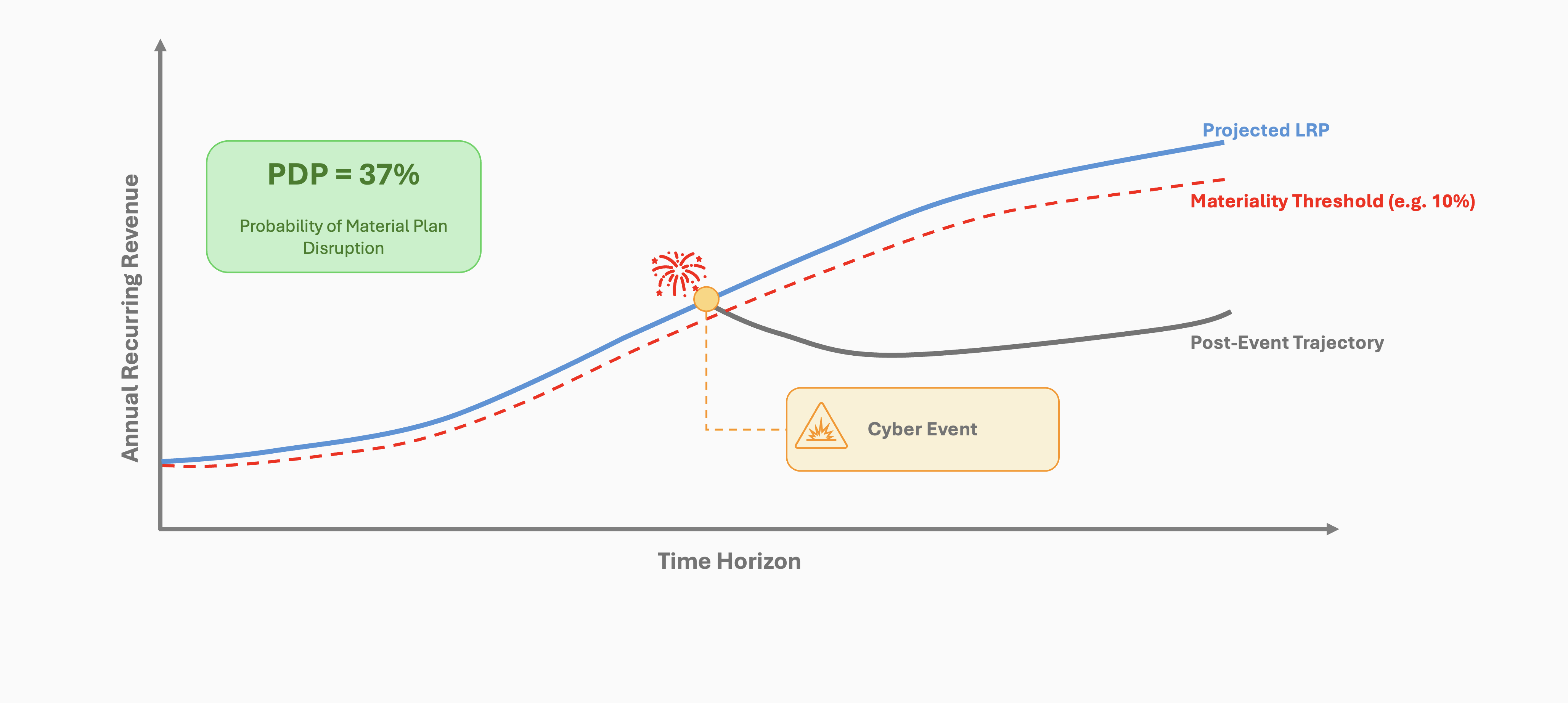
Tier 0 risk analysis represents the pinnacle of strategic-level cybersecurity assessment. It evaluates how potential cybersecurity events could impact critical business objectives and future plans. By integrating insights from all other risk tiers, Tier 0 analysis provides executive leadership with a comprehensive view of cyber risks in the context of broader business strategies, enabling informed decision-making at the highest organizational levels.
Tier 0 Risk Analysis: Strategic Cybersecurity Assessment
The primary goals of Tier 0 risk assessment are to:
- Drive strategic decision-making based on probable risk outcome futures
- Align cybersecurity strategy with overall business objectives
- Facilitate high-level discussions on cyber risk at board and executive levels
While Tier 0 analysis incorporates results from all other tiers, its objective is to distill this information into strategic insights. The underlying details from lower tiers provide rigor and traceability but are not necessarily surfaced in executive or board conversations. However, this detailed information remains available for those who wish to delve deeper into the analysis.
Application of Tier 0 risk
Here are a few examples of how you may use Tier 0 risk analysis:
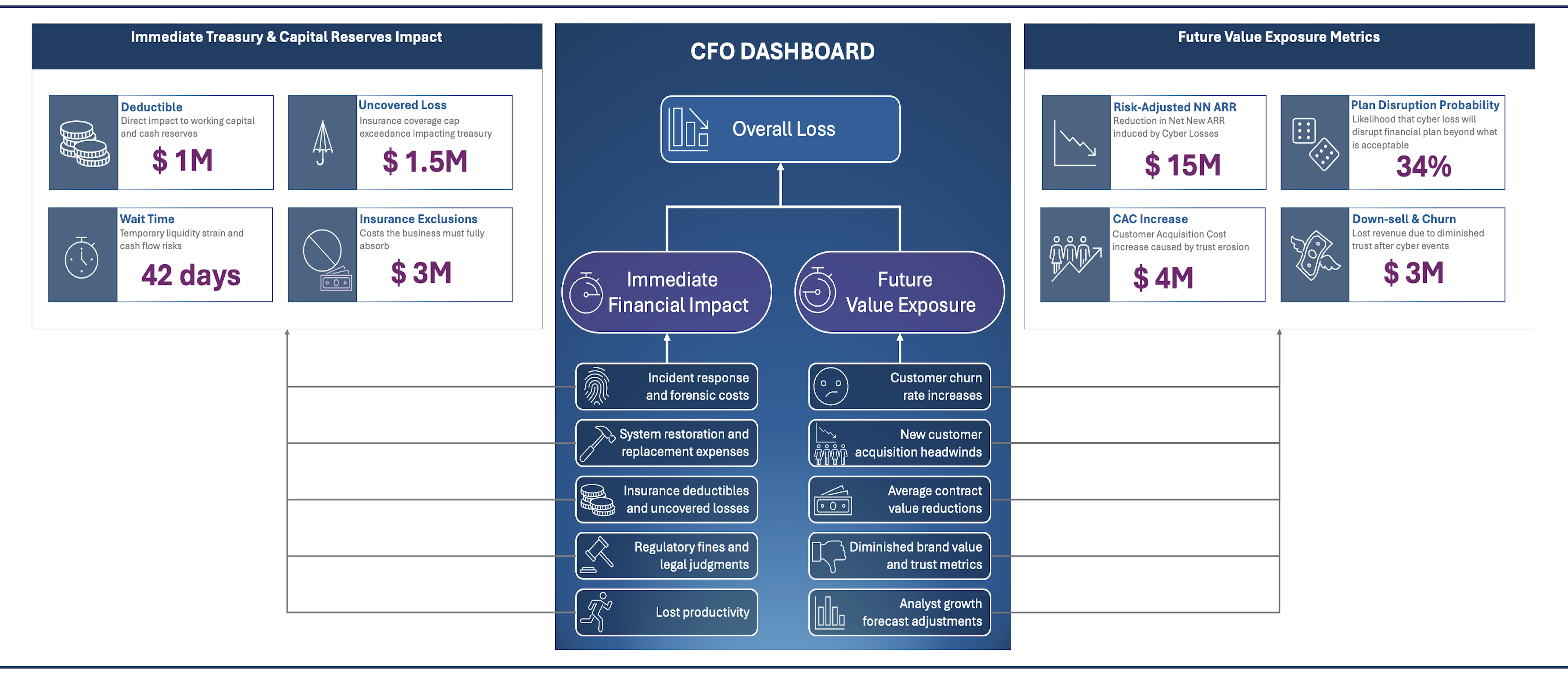
Provide an assessment of probable impact of material cybersecurity events on an IPO, or a geographic expansion plan, or merger and acquisition plans to your board or executive leadership team.
Provide an analysis of the chances of meeting growth targets, given the occurrence of one or more material cybersecurity events to your Chief Finance Officer or Chief Revenue Officer.
Collaborate with and support your CFO in producing a risk-adjusted financial forecast for the board.
The following are key considerations for Tier 0 analysis:
- Integration of other Tiers: Incorporate results from Tiers 1, 2, and 3 to ensure a comprehensive and well-grounded analysis.
- Executive-Level Communication: Present information in a manner suitable for board and executive leadership team discussions, focusing on strategic implications rather than technical details.
- Collaborative Approach: Work closely with other C-suite members, particularly the CFO, to align cybersecurity risk assessments with overall business risk management.
- Scenario Planning: Develop and analyze various future scenarios incorporating potential cyber events and their business impacts.
- Risk-Adjusted Forecasting: Assist in creating financial projections that account for potential cybersecurity incidents.
- Traceability and Depth: Ensure that detailed supporting data from lower tiers is available for those who wish to delve deeper into the analysis.
- Continuous Update: Regularly revisit and update the Tier 0 analysis to reflect changes in the business environment and cyber threat landscape.
- Strategic Alignment: Ensure that the risk analysis directly informs and supports key strategic decisions and long-term planning.
By addressing these elements, Tier 0 risk analysis provides a crucial link between cybersecurity concerns and high-level business strategy, enabling your organization to navigate uncertain futures with greater confidence and preparedness.
Conclusion
The tiered approach to quantitative risk assessment offers CISOs and security leaders a powerful framework for addressing cybersecurity challenges across all levels of the organization. By integrating tactical metrics (Tier 3), operational controls and attack paths (Tier 2), impact scenarios (Tier 1), and strategic business objectives (Tier 0), this model provides a comprehensive view of an organization’s risk landscape.
This hierarchical structure enables security teams to:
- Ground decisions in data-driven insights
- Effectively communicate risk at all organizational levels
- Align cybersecurity efforts with business strategies
- Optimize resource allocation and control investments
- Proactively address emerging threats
By adopting this tiered risk analysis approach, CISOs can transform their role from mere gatekeepers to strategic enablers of business growth and innovation. In an era of rapidly evolving digital threats, this model equips organizations with the tools needed to navigate uncertainty, make informed decisions, and drive sustained success in the face of complex cybersecurity challenges.