· Dayo Adetoye (PhD, C|CISO) · Managing Uncertainty and Complexity · 3 min read
Thriving in the VUCAH Landscape:
Advanced Risk Management Strategies for CISOs
Embrace and win under complexity and uncertainty: how to measurably manage risk within appetite

The modern cybersecurity leader must not only manage risk in an ever-evolving threat landscape, but must also partner with the business to achieve business objectives.
In this article, we will focus on the former imperative: that of managing risk in a highly volatile, complex, and uncertain environment, which requires a set of skills and strategies. By mastering these, we can measurably manage risk within our appetite and thrive in this environment.
The VUCAH Theatre of Operation
To describe the threat landscape, the acronym VUCAH (Volatile, Uncertain, Complex, Ambiguous, and Hyper-connected) perfectly captures the environment we operate within. Each of these descriptions has specific attributes that lend themselves to strategies and mindset that the CISO must adopt to effectively manage risk and thrive.
- Volatile: The threat landscape is constantly evolving, making it challenging to predict and respond to emerging threats.
- CISO Response: Incorporate Threat intelligence, scenario planning, red teaming exercises and continuous attack surface management to understand threat landscape and your susceptibility.
- Uncertain: The nature of the cyber threats is not always clear, and making rational risk management decision involves embracing probabilistic techniques and evidence-driven belief update.
- CISO Response: Embrace Bayesian updating, adopt Monte Carlo Techniques to quantify risk, invest in threat hunting capabilities, use the outcomes of your continuous testing to update your belief about your resistance to threats. Plan for tail risk, resilience, recovery and antifragility.
- Complex: Your environment is complex, involving technologies, imperfect people (who can make mistakes or be malicious), and imperfect processes. Threats in your environment are often multi-faceted and require a comprehensive approach to address.
- CISO Response: Adopt the Cynefin methodology of frequent probing for complex system by continuously validating your controls (pen-testing, business continuity and disaster recovery, continuous attack surface monitoring, breach simulation etc.), utilize quantitative risk frameworks.
- Ambiguous: The intent and motives of actors are not always clear, making it challenging to identify and respond to malicious activities. Your board and C-Suites will not give you concrete risk appetite.
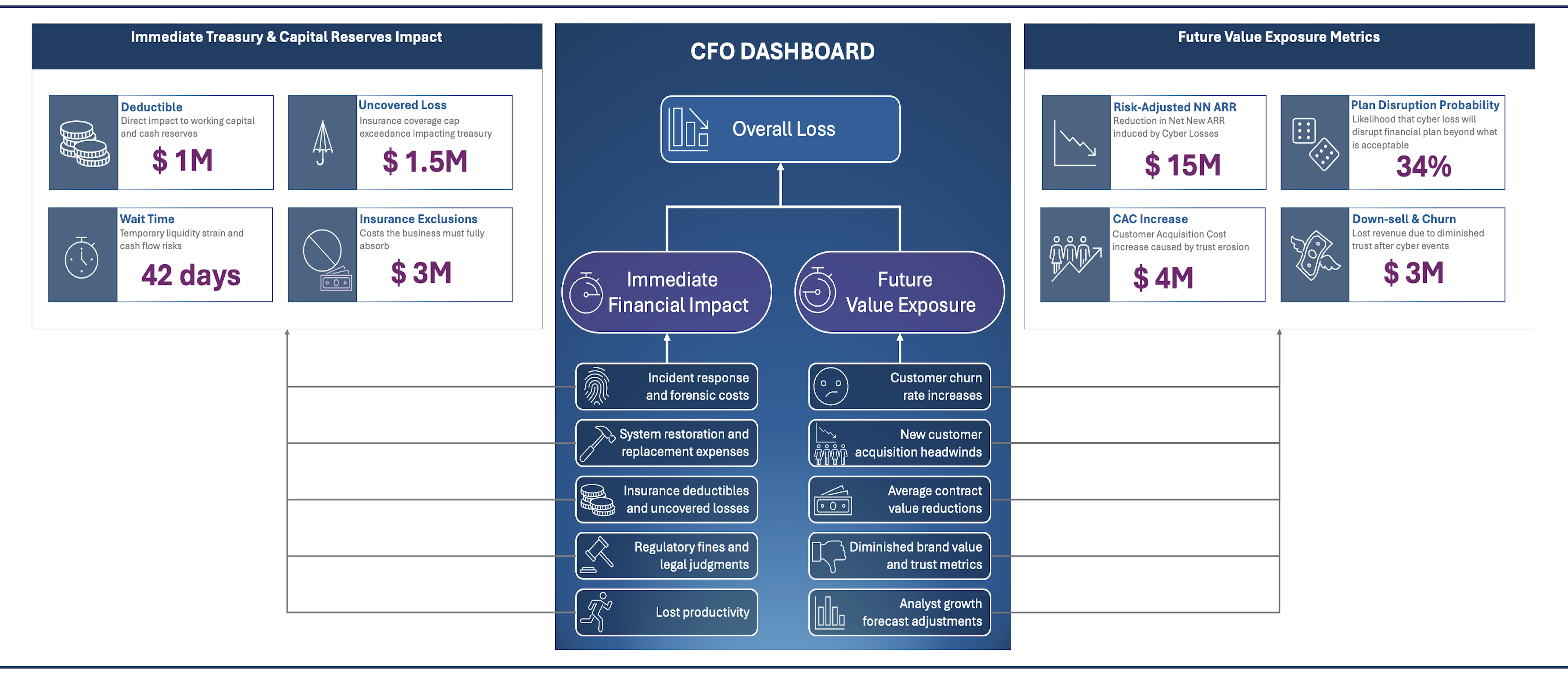
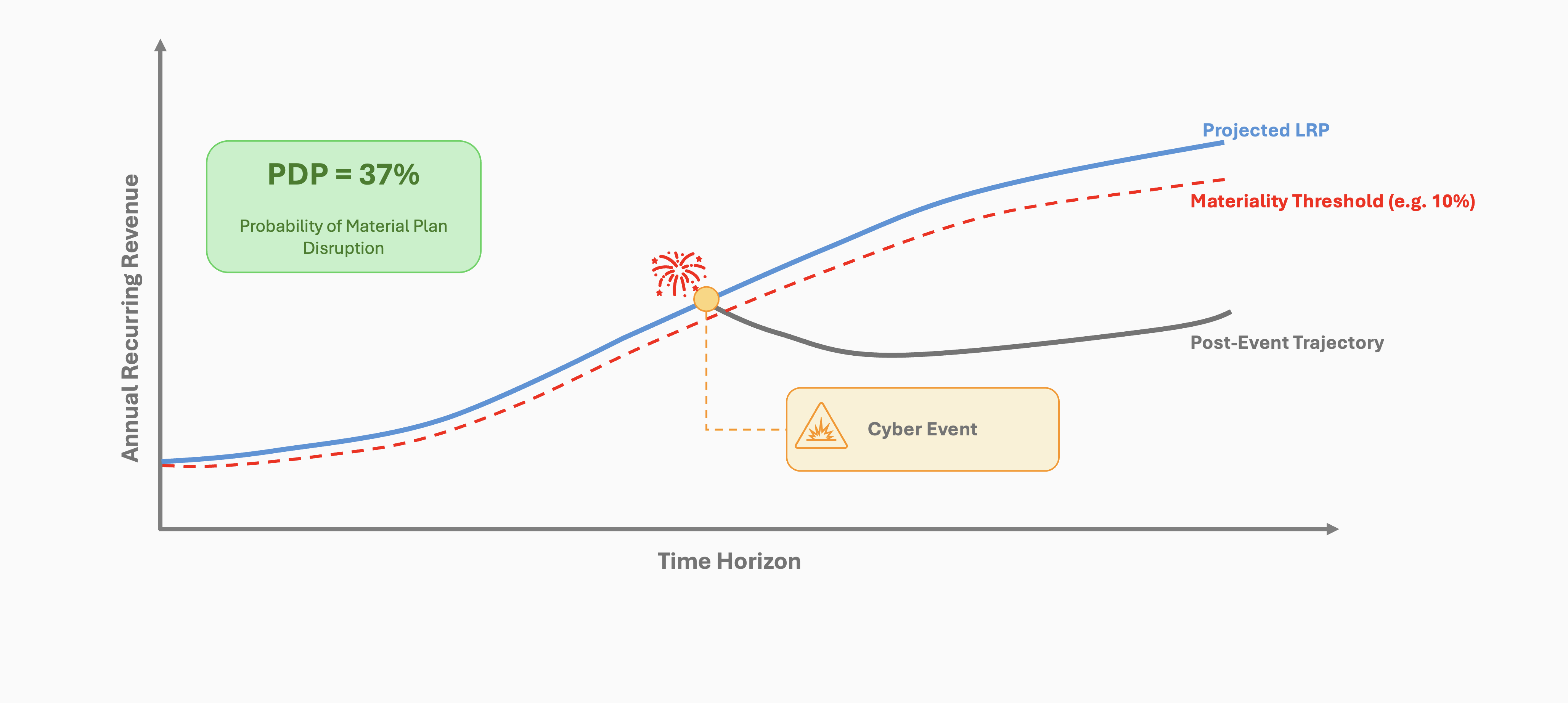
- CISO Response: Embrace Red Team (Critical) Thinking techniques to identify your own blind spots and biases, distil your board’s qualitative risk appetite to more concrete quantified risk appetite, and let the board approve that as well as your strategy for managing the quantified risk. For example, there is a 50% chance that the business will suffer a loss greater than $1 million and 5% chance that it will be greater than $10 million etc. over the next financial year, but here are the possible futures if we took the following actions: Portfolio A: Cost: $100k per anum, 20% chance loss greater than $1 million and 1% chance to exceed $10 million vs Portfolio B: Cost: $50k per anum, 45% chance loss greater than $1 million and 4% chance to exceed $10 million. You are using quantitative Monte Carlo risk simulation frameworks, right?
- Hyper-connected: The interconnectedness of systems and networks makes it easier for threats to spread and have a broader impact. Your supply chains are attack vectors with resultant risks accruing.
- CISO Response: Make Zero Trust principles a fundamental architectural pattern. Invest in supply chain risk management.
To effectively manage risk in this environment, we must adopt a strategic approach that balances risk mitigation with business agility.
The key point is to be strategic in your approach, and to demonstrate that you can measurably manage risk within appetite, applying fiscal prudence to enable your business to thrive in a complex and uncertain adversarial theatre of operation.