· Dayo Adetoye (PhD, C|CISO) · Partnering with the Business · 8 min read
The Strategic Importance of the Modern CISO:
Collaborating for Business Growth and Value Protection
The modern CISO's role has evolved from mere gatekeeper to growth enabler, necessitating collaboration with peers to elevate cybersecurity's strategic value to executive leadership.

From Gatekeeper to Growth enabler
The days of the CISO as a security gatekeeper are over. Today’s cybersecurity leaders drive business growth, trust, and operational efficiency.
By balancing risk and productivity, a modern CISO fosters secure customer experiences that enhance trust, streamline onboarding, and accelerate time-to-market. Effective security reduces breach risks, strengthens compliance with industry certifications, and unlocks new revenue opportunities. These factors collectively improve brand reputation, position the company as a trusted partner, and directly contribute to business growth and customer acquisition.
On the operational side, a CISO’s deep understanding of risk enables clear, data-driven decision-making that aligns security with business objectives. By helping the organization manage risk within appetite, the CISO ensures fiscal prudence while supporting strategic initiatives that enhance efficiency, resilience, and overall productivity.
Evolving Role
The modern CISO has evolved from gatekeeper to growth enabler. By embedding security by design as a core business principle and leveraging modern risk management frameworks, they create conditions where innovation and growth thrive safely, ensuring security is a catalyst - not a constraint - for strategic decision-making.
This transformation requires closer collaboration with executive peers to showcase cybersecurity’s strategic value to the business. To do this effectively, today’s CISO must pair technical expertise with business acumen.
In this article, we’ll explore how CISOs can go beyond protection - becoming key enablers of growth, trust, and innovation through strategic collaboration and partnership.
Collaboration Opportunities
To succeed, the modern CISO must actively partner with fellow C-suite executives, ensuring tight alignment between cybersecurity strategy and business objectives. This requires two-way collaboration, where the CISO not only understands the company’s goals but also clearly articulates how security enables them.
Meet Them Where They Are!
Let’s face it - security teams often battle stubborn stereotypes: the friction creators, the department of “No,” the cost center. The modern CISO must rise above these outdated perceptions, embracing a proactive, solution-oriented approach to partnership and collaboration.
- Don’t wait for an invitation - go meet other leaders on their turf and offer solutions!
Here are a few collaboration opportunities, tailored to key C-suite executives. Adapt them to fit your business needs.
CEO: Strategic Partnership for Resilient Growth
- Establish a Cyber Risk Dashboard that translates technical threats into clear business impacts, reviewed regularly in executive meetings. See Business Enablement Metrics for examples.
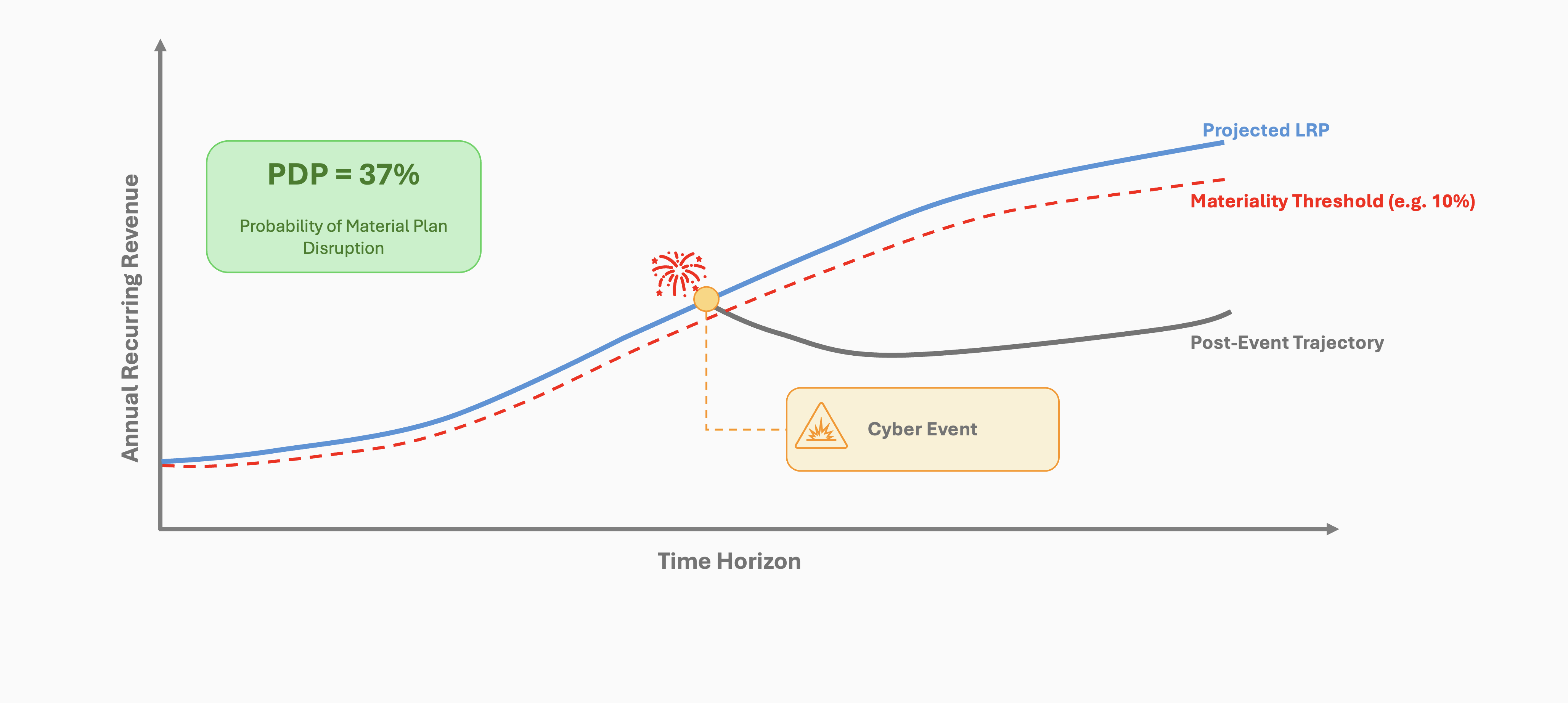
- Align security initiatives with the CEO’s strategic vision, using Plan Disruption Probability (PDP) to frame cyber risk in terms of financial resilience, business continuity, digital transformation, and risk appetite.
CFO: Financial Alignment & Risk-Informed Investment
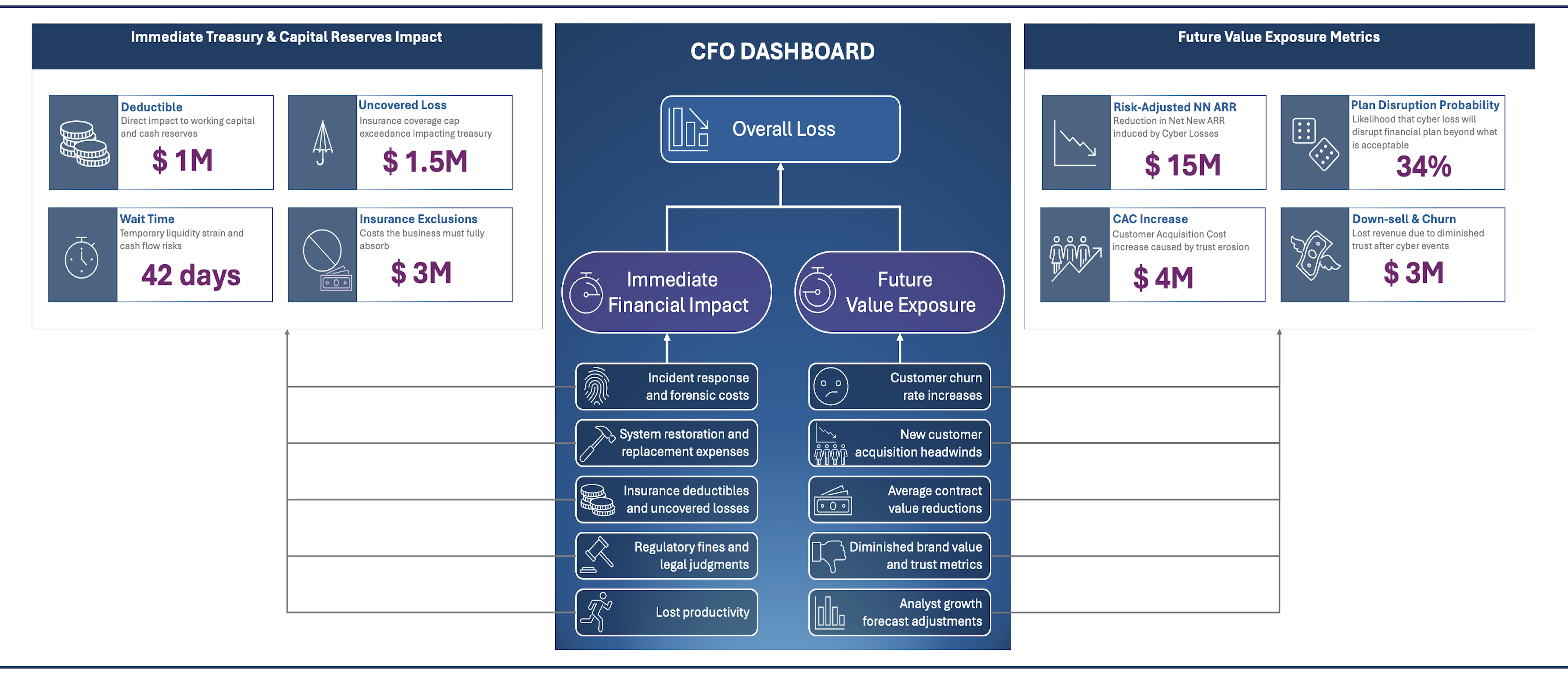
- Deliver a Cyber ROI Report that quantifies how security investments protect financial outcomes, reduce risk exposure, and enhance operational efficiency. Support with PDP, Fiscal Prudence, and Risk-Adjusted Growth Forecast metrics.
- Collaborate on a cyber insurance and risk transfer strategy, ensuring coverage aligns with financial risk tolerance and exposure modeling. See examples of how to do this with a CFO Dashboard.
Chief Revenue Officer (CRO): Growth-Ready Security
- Design a Secure Customer Onboarding experience that embeds security without impacting sales velocity - balancing trust and speed.
- Enable go-to-market teams with security value messaging, positioning cybersecurity as a competitive differentiator and trust enabler in sales conversations.
Chief Marketing Officer (CMO)
- Co-create a Cyber Trust Campaign that reinforces the company’s commitment to data protection and security.
- Implement secure social media management tools and train marketing teams on cybersecurity best practices.
Chief Operations Officer (COO)
- Conduct joint business continuity exercises, integrating cybersecurity scenarios into operational resilience planning.
- Embed “Security by Design” into new operational processes and technology initiatives, ensuring security is a foundational principle rather than a bolt-on.
Chief Technology Officer (CTO) / Chief Information Officer (CIO)
- Launch a “Secure Innovation Lab” to test emerging technologies for security implications before full-scale deployment.
- Develop a “Tech Stack Security Roadmap”, ensuring security upgrades align with technology refresh cycles for seamless adoption.
- Implement a “Shared Security Responsibility” model, where technical teams own the security of the platforms they manage, fostering accountability.
- Prioritize “Productivity and Efficiency” as key drivers of growth. Partner with technology leaders to develop secure AI-driven automation tools that streamline workflows while maintaining a balanced approach to risk and productivity.
- While traditionally-minded CISOs may hesitate to prioritize productivity and operational efficiency, the modern CISO understands that security and productivity are not mutually exclusive - but rather, a strategic lever for business enablement.
Chief Product Officer (CPO)
- Integrate security threat modeling and testing into the product development lifecycle, providing developers with rapid, actionable security feedback.
- Reduce friction and accelerate innovation through security automation, ensuring security enhances - rather than impedes - the development process.
- Co-sponsor a Security Champions Program, recognizing and rewarding employees who advocate for security within product teams.
- Co-develop “Security as a Feature” elements that can be highlighted in product marketing, turning security into a competitive advantage.
Chief Customer Officer
- Launch a “Customer Security Portal” - a transparent dashboard where clients can view their data protection measures, compliance status, and security certifications.
- Establish a customer-facing security communication strategy to proactively share security updates, best practices, and incident response protocols, reinforcing trust and confidence.
Chief Data Officer
(If you’re also wearing the CDO or Chief Privacy Officer hat, this section may already be in your scope. If not, collaboration is key!)
- Implement a “Data Classification and Protection” framework that aligns security controls with data sensitivity and business value.
- Co-develop data governance policies that strike the right balance between accessibility and security, enabling data-driven decision-making without unnecessary risk.
- Ensure alignment with regulatory and compliance requirements by working closely with Legal, GRC, and Privacy teams to integrate classification and governance policies into broader compliance frameworks.
Chief Legal Officer / General Counsel & Compliance Teams
- Develop a “Cyber Risk & Regulatory Alignment Framework” to ensure security policies and controls proactively address evolving legal, regulatory, and contractual obligations. This minimizes compliance risks while enabling business agility.
- Establish a streamlined “Incident Disclosure Playbook” that aligns legal, compliance, and security teams on breach notification requirements, regulatory reporting, and customer communications - ensuring fast, coordinated responses.
- Collaborate on Third-Party Risk Management by integrating security assessments into vendor contracts, ensuring legal and compliance teams have visibility into cybersecurity risks in the supply chain.
- Enhance Privacy & Data Protection Programs by co-developing policies that align security controls with data retention, processing, and cross-border data transfer requirements, strengthening compliance with laws like GDPR and CCPA.
- Support Secure AI Governance by working together to establish policies that balance innovation with ethical, legal, and security considerations for AI-driven initiatives.
Chief Human Resources Officer
- Design a gamified “Security Awareness Program” that rewards employees for adopting good security habits. Adopt a Modern Human Risk approach to improve employee security awareness and reduce incidents. Avoid the outdated “gotcha” approach - your goal is to build a security-first culture, not play “security cop”.
- Integrate security into job descriptions and performance reviews by creating a “Cyber Skills Matrix”, making security a core competency across all roles - not just an IT concern.
Additional Collaboration Enhancers for the CISO
Cross-functional Security Council: Hold monthly meetings with representatives from each C-suite function to discuss the security implications of upcoming business initiatives.
Executive Security Shadowing: Implement a program where you “spend a day” with each C-suite executive to better understand their challenges and identify key security touchpoints. Use this time to align on strategy and ensure everyone is on the same page. Tailor your approach for each C-suite role to address their specific concerns.
Cyber War Room Simulations: Conduct quarterly tabletop exercises or pre-mortems with all C-suite members to practice coordinated responses to major security incidents. Use these simulations to present the “State of Risk Exposure” based on your quantified risk assessment. Highlight tail risks, trends, and how your organization compares to peers in your sector. This is also your opportunity to showcase how your strategy is keeping risks within appetite or to identify areas needing more attention.
Security Innovation Awards: Launch an annual award to recognize departments or individuals who’ve successfully integrated security into their business processes or made significant strides in improving key security metrics.
Cyber Risk Appetite Workshops: Facilitate workshops with the C-suite to define and align on the organization’s cyber risk appetite, ensuring a shared understanding of security priorities.
Conclusion: The CISO as Business Catalyst
The Modern CISO's Measure of Success
The most successful CISOs today aren’t defined by the breaches they prevent but by the business opportunities they enable.
As a modern CISO, by gaining a deep understanding of your organization’s strategic goals and fostering meaningful partnerships across the C-suite, you can transform security from a technical function into a true business catalyst.
This transformation requires more than just technical expertise; it demands business acumen. Invest in enhancing your communication skills, business literacy, and strategic thinking alongside your security knowledge.
The future belongs to CISOs who can demonstrate how security drives speed, builds trust, and creates a competitive advantage. By adopting the partnership strategies outlined above, you’ll position yourself - and your organization - for success in an increasingly complex digital landscape.