· Dayo Adetoye (PhD, C|CISO) · Advanced Practices · 20 min read
Reimagining Human Risk:
How to Measure and Manage it.
Your biggest security threat isn't malware - it's Mark from Accounting. Human risk in cybersecurity is a dynamic challenge that directly impacts organizational resilience and profitability. From employees and contractors to partners, human behaviors and errors are often the catalysts for breaches and business disruptions. This article explores how to measure and manage human risk, focusing on actionable insights, predictive modeling, and risk indicators that help organizations stay ahead. By turning the human element from a vulnerability into a strength, leaders can build a more secure and resilient business foundation.

Every second, somewhere in the world, an employee clicks a suspicious link. Another shares sensitive data through an unsecured channel. And a third uses “Password123!” to protect critical systems. These aren’t just isolated mistakes - they’re ticking time bombs in your organization’s cybersecurity landscape.
The numbers tell a sobering story: 76% of data breaches involve the human element, whether through malicious intent or unintentional error, according to the Verizon 2024 Data Breach Investigations Report. The financial implications are staggering too: the IBM and Ponemon Institute’s 2024 Cost of a Data Breach Report reveals an average breach cost of $4.88 million. This can result in reputational damage that can devastate an organization for years. Despite these critical risks, most organizations continue to treat human risk as an abstract concept, reducing it to simplistic metrics like annual training completion rates and phishing test scores.
Are We Even Asking the Right Questions?
Instead of “How do we stop our people from making mistakes?” perhaps we should ask: “How do we measure, predict and deploy mitigating interventions to harness and improve human behavior and thus build genuine cyber resilience?” This isn’t just about identifying vulnerabilities - it’s about gaining a deep understanding of the drivers of your risk and turning it around through proactive strategic interventions and by building a security culture that dynamically adapts to and responds to emerging threats.
Why Current Approaches Fall Short
Traditional human risk management in cybersecurity relies heavily on annual awareness training and periodic phishing simulations - approaches that research has shown to offer limited value. This conventional wisdom fails on multiple fronts:
Disconnected from Business Risk
- Fails to correlate access privileges with potential business impact
- Overlooks how routine job functions can amplify risk exposure (e.g., IT administrators with system-wide access)
- Disregards how specific roles can trigger significant losses (e.g., finance staff authorizing wire transfers)
- Treats all users equally despite vastly different risk potentials based on their access levels
Limited Scope
- Focuses exclusively on employees, ignoring contractors, consultants, and suppliers with system access
- Treats human risk as a training problem rather than a complex behavioral challenge
- Assumes periodic interventions can address constantly evolving threats
One-Size-Fits-All Approach
- Ignores individual risk profiles and behavioral patterns
- Applies the same solutions to both accidental mistakes and malicious actions
- Disregards context-specific risk factors
Reactive Rather Than Predictive
- Responds to incidents after they occur
- Fails to identify emerging risk patterns
- Lacks real-time monitoring and intervention capabilities
The reality is stark: human-facilitated cyber threats are dynamic and unpredictable. They can’t be effectively managed through monthly phishing tests or quarterly awareness sessions. Organizations need a fundamental shift from periodic training to continuous human risk intelligence.
This article will examine practical approaches that go beyond traditional awareness metrics. We’ll explore how your organization can take a data-driven approach, combining security incident data with behavioral indicators to create predictive risk models. These insights will give you powerful tools to anticipate and prevent human-triggered security incidents before they occur. The stakes couldn’t be higher: in an era where a single click can cost millions, understanding your human risk isn’t just good security - it’s business survival.
Continuous Human Risk Intelligence
Our analysis of traditional approaches revealed critical gaps in human risk management. Now, let’s explore a more effective paradigm: Human Risk Intelligence - a continuous predictive model that drives targeted interventions to reduce business risk materialization.
The Human Risk Intelligence Model
To effectively manage human risk, we must first quantify it. This brings us to our human risk intelligence model, which measures and predicts the material risk that could result from human actions within our technical environment.
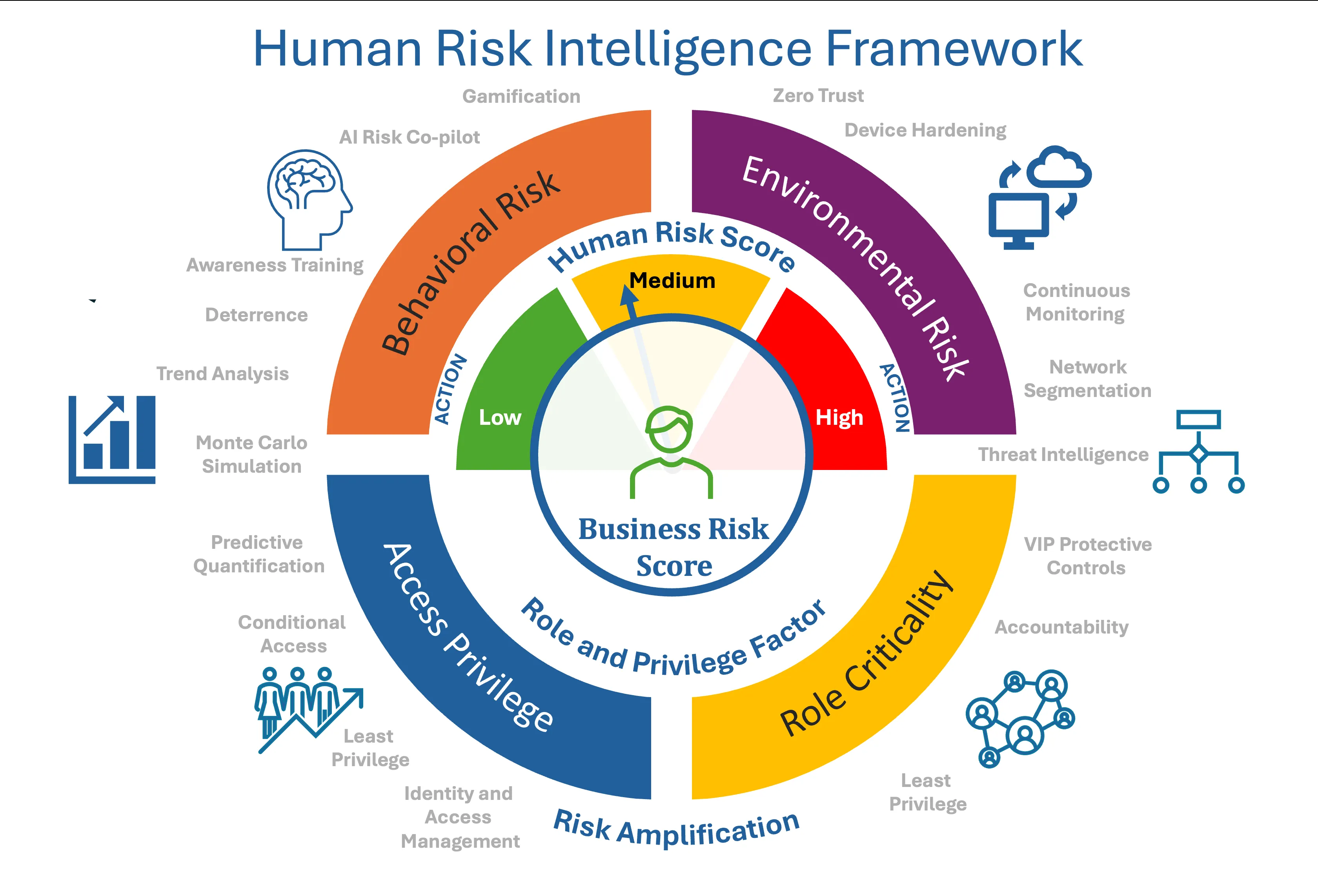
Human Risk Scoring Model
At the heart of continuous human risk intelligence lies the Business Risk Score (BRS) - a comprehensive metric that quantifies potential risk based on both human behavior and business context.
Core Components of the Business Risk Score
Human Risk Score (HRS)
Measures risk probability based on observed behaviors and actions that impact the security of the technical environment
Components:
- Behavioral Risk (B): Evaluates user actions
- Positive indicators (risk-reducing), examples:
- Reporting suspicious emails
- Following security protocols
- Using approved tools
- Negative indicators (risk-increasing), examples:
- Clicking malicious links
- Sharing credentials
- Violating security policies
- Positive indicators (risk-reducing), examples:
- Environmental Risk (E): Assesses user’s action on technical environment. Examples include:
- Detonating malware
- Disabling security controls and other security misconfigurations
- Timely Patching (risk-reducing)
- Configures encryption for sensitive files (risk-reducing)
- Behavioral Risk (B): Evaluates user actions
Uses Bayesian updating for continuous refinement
Role & Privilege Factor (RPF)
- Measures the potential amplification of risk based on a user’s organizational role and system access privileges
- Components:
- Role Criticality (RC): Establishes a baseline risk based on the user’s authority and influence in the organization (e.g., interns vs. C-Suite).
- Access Privileges (AP): Represents the cumulative risk associated with the systems and data the user can access, weighted by their criticality.
- Uses asymptotic growth model to reflect diminishing risk returns
Business Risk Score Calculation
Where:
- HRS ∈ [0,1]: Probability of risk materialization, updated dynamically as actions occur
- RPF ∈ [0,1]: Impact multiplier based on role and access, evolves with organizational and technical permission changes
Practical Applications
The BRS can serve multiple critical functions:
Risk Quantification
- Convert abstract risk into measurable metrics
- Enable comparison across users and departments
- Facilitate trend analysis
Real-time Monitoring
- Continuous risk assessment
- Immediate response to behavior changes
- Early warning system for emerging threats
Resource Allocation
- Prioritize high-risk users for intervention
- Guide security investment decisions
- Optimize training and awareness programs
Automated Response
- Trigger access restrictions based on risk thresholds
- Initiate additional monitoring and deterrence messaging for high-risk scenarios
- Deploy targeted security controls
This model transforms human risk management from a periodic assessment into a dynamic, data-driven process that adapts to changing behavior patterns and business contexts.
Now let us examine the definition of HRS and RPF in detail.
Human Risk Score (HRS):
The HRS reflects the user’s overall risk level based on their behavior (Behavioral Risk, B) and technical environment impact of their actions (Environmental Risk, E). Using Bayesian principles:
Where:
- : Positive evidence from Behavioral Risk (good user actions).
- : Positive evidence from Environmental Risk (improved environment).
- : Negative evidence from Behavioral Risk (bad user actions).
- : Negative evidence from Environmental Risk (environmental vulnerabilities).
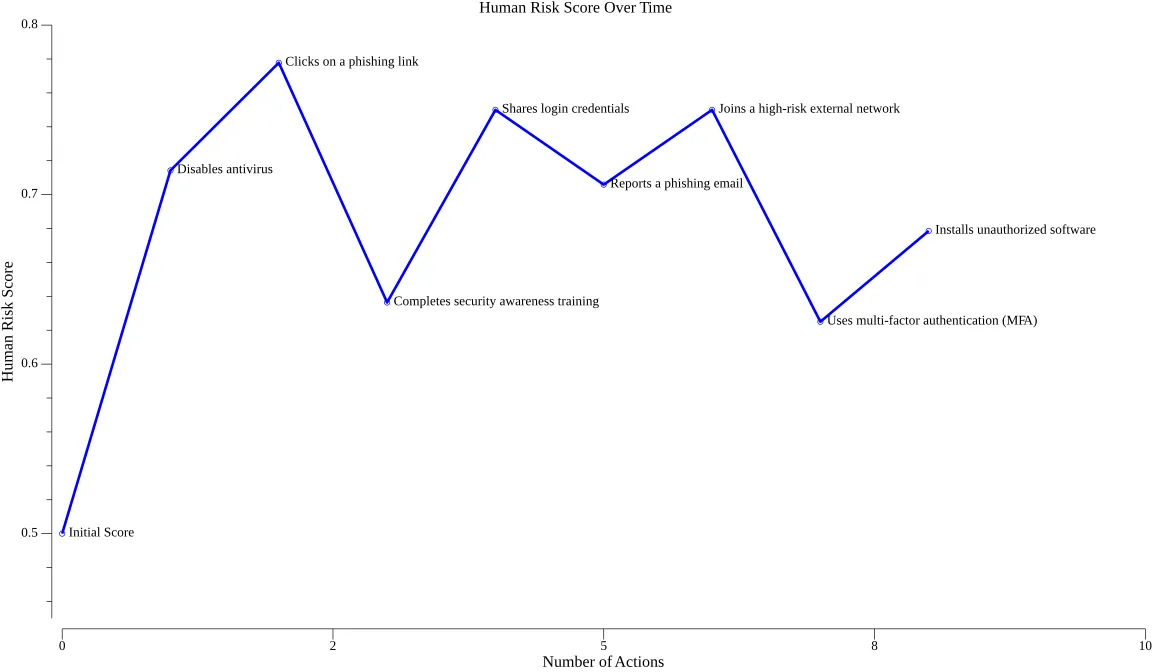
The HRS has a powerful underlying “memory” feature as more data evidence, based on user actions, is gathered, it builds a stable model of the user’s overall score that is not extremely sensitive to one-off actions, representing a long-term and truly data-driven view of the user’s risk posture.
We provide an example of how user actions may be mapped to the behavior and environmental risk below.
To illustrate the mapping of various user actions to calculate the HRS for users, we provide some examples of (positive: and negative: ) user actions and how they might be weighted along behavioral or environmental risk axes. These values demonstrate how different types of activities might impact the Behavioral Risk (B) and Environmental Risk (E) components of the Human Risk Score (HRS).
Key Observations
Positive Actions ():
- Focused on improving user behavior (e.g.,training, vigilance) and reducing environmental exposure (e.g., securing systems, restricting access).
Negative Actions ():
- Reflect bad user behavior (e.g., negligence, ignoring training) or actions that increase environmental risk (e.g., exposing data, failing to patch systems).
This table also provides a good starting point for identifying data sources for relevant actions in the continuous human risk intelligence model.
User Actions and Proposed Impact on HRS
| # | User Action | Comments | ||||
|---|---|---|---|---|---|---|
| 1 | Completes security awareness training | +2 | 0 | 0 | 0 | Improves user behavior awareness. |
| 2 | Reports a phishing email | +1 | 0 | 0 | 0 | Positive behavior, vigilance against threats. |
| 3 | Uses multi-factor authentication (MFA) | +3 | +1 | 0 | 0 | Strong improvement in both behavioral and environmental security. |
| 4 | Changes password regularly | +1 | 0 | 0 | 0 | Basic positive action showing compliance. |
| 5 | Disables antivirus | 0 | 0 | 0 | +3 | Significant environmental risk. |
| 6 | Clicks on a phishing link | 0 | 0 | +2 | 0 | Risky user behavior with potential exposure. |
| 7 | Shares login credentials | 0 | 0 | +3 | +2 | High-risk behavior with environmental exposure. |
| 8 | Joins a high-risk external network | 0 | 0 | +1 | +2 | Increases environmental risk. |
| 9 | Installs unauthorized software | 0 | 0 | +2 | +2 | Risky action potentially introducing vulnerabilities. |
| 10 | Ignores security alerts | 0 | 0 | +1 | +1 | Negligence in addressing potential risks. |
| 11 | Removes admin privileges | 0 | +3 | 0 | 0 | Strong reduction in environmental risk. |
| 12 | Completes role-specific security training | +2 | 0 | 0 | 0 | Focused improvement in behavior for specific job functions. |
| 13 | Reports a suspicious network activity | +2 | +1 | 0 | 0 | Vigilance in monitoring and reporting threats. |
| 14 | Updates device software regularly | 0 | +2 | 0 | 0 | Environmental improvement by reducing vulnerabilities. |
| 15 | Configures strong passwords | +1 | 0 | 0 | 0 | Basic positive behavior. |
| 16 | Falls victim to a social engineering scam | 0 | 0 | +2 | 0 | Behavioral lapse with significant risk exposure. |
| 17 | Reports a suspected social engineering attempt | +2 | 0 | 0 | 0 | Positive behavior showing vigilance. |
| 18 | Leaves workstation unlocked | 0 | 0 | +2 | 0 | Behavioral negligence. |
| 19 | Retains unused admin privilege (e.g. for 30 days) | 0 | 0 | 0 | +2 | Risk of abuse if user account is compromised. Lack of permission rightsizing. Consider just-in-time permissions. |
| 20 | Fails to report a suspected phishing email | 0 | 0 | +1 | 0 | Behavioral lapse in vigilance. |
| 21 | Patches a critical system vulnerability | 0 | +3 | 0 | 0 | Strong reduction in environmental risk. |
| 22 | Fails to patch a known vulnerability | 0 | 0 | 0 | +2 | Environmental risk due to negligence. |
| 23 | Shares sensitive data on public platforms | 0 | 0 | +3 | +2 | Behavioral and environmental risk. |
| 24 | Downloads an attachment from an unknown email | 0 | 0 | +2 | +1 | Risky behavior with potential environmental exposure. |
| 25 | Uses personal email for work purposes | 0 | 0 | +1 | +1 | Increased exposure to phishing attacks. |
| 26 | Configures email spam filters | +1 | +1 | 0 | 0 | Behavioral and environmental improvement. |
| 27 | Bypasses IT controls to access restricted systems | 0 | 0 | +3 | +2 | High-risk behavior with major environmental exposure. |
| 28 | Repeatedly fails MFA attempts | 0 | 0 | +1 | 0 | Indicates possible negligence or a compromised account. |
| 29 | Transfers sensitive data without encryption | 0 | 0 | +2 | +2 | Significant environmental and behavioral risk. |
| 30 | Configures a VPN for remote work | +1 | +2 | 0 | 0 | Strong environmental improvement for secure access. |
| 31 | Leaves credentials exposed in plain text | 0 | 0 | +3 | +2 | Critical risk due to exposed credentials. |
| 32 | Detects and stops a phishing attempt | +2 | +1 | 0 | 0 | Vigilance and environmental security improvement. |
| 33 | Forgets to log out of shared systems | 0 | 0 | +2 | 0 | Behavioral negligence increasing access risks. |
| 34 | Uses weak passwords for critical systems | 0 | 0 | +2 | +2 | High risk for critical systems. |
| 35 | Correctly escalates a potential insider threat | +2 | +1 | 0 | 0 | Positive behavior and environmental vigilance. |
| 36 | Participates in phishing simulation and passes | +1 | 0 | 0 | 0 | Behavioral improvement through training. |
| 37 | Fails a phishing simulation test | 0 | 0 | +2 | 0 | Indicates susceptibility to phishing. |
| 38 | Reports insider threat activity | +2 | +2 | 0 | 0 | Strong improvement in both behavior and environmental vigilance. |
| 39 | Configures endpoint protection tools | 0 | +3 | 0 | 0 | Environmental improvement through technical controls. |
| 40 | Disconnects from a suspicious network | +1 | +2 | 0 | 0 | Behavioral and environmental improvement. |
| 41 | Ignores mandatory cybersecurity training | 0 | 0 | +2 | 0 | Behavioral lapse. |
| 42 | Reports malware activity | +2 | +2 | 0 | 0 | Strong vigilance in both behavior and environment. |
| 43 | Installs patches on personal devices used for work | 0 | +2 | 0 | 0 | Reduces environmental risk for bring-your-own-device scenarios. |
| 44 | Logs into a suspicious external website | 0 | 0 | +1 | +1 | Increases exposure to potential threats. |
| 45 | Detects and blocks suspicious emails | +2 | +1 | 0 | 0 | Vigilance in threat detection. |
| 46 | Configures encryption for sensitive files | 0 | +3 | 0 | 0 | Significant reduction in environmental risk. |
| 47 | Leaks internal information accidentally | 0 | 0 | +2 | +2 | Behavioral and environmental negligence. |
| 48 | Detects and mitigates suspicious insider activity | +2 | +2 | 0 | 0 | Major improvement in vigilance and risk response. |
| 49 | Downloads unverified software from external sources | 0 | 0 | +2 | +2 | High-risk action introducing potential vulnerabilities. |
| 50 | Configures role-based access controls | 0 | +3 | 0 | 0 | Reduces environmental risk by restricting access. |
With this we can now track user’s Human Risk Score evolution over time as demonstrated below.
Role & Privilege Factor (RPF):
The RPF reflects the risk contribution from the user’s role and access privileges. It combines Role Criticality (RC), Access Privileges (AP) as a risk amplification factor:
Where:
- RC: The Role Criticality, setting the baseline (floor) for the user RPF.
- AP: The sum of the user’s access privileges, where each type of privilege is assigned a risk-weighted value.
- : An access privilege growth factor, controlling how quickly the RPF approaches 1 as AP increases. This captures your business’ tolerance for risk as user privileges increase.
A key concept behind the Role & Privilege Factor (RPF) is that the impact of a user’s actions varies depending on their role and access level, even if the actions themselves are identical. For instance, an IT administrator detonating malware on their workstation could have significantly different consequences compared to a receptionist doing the same. Similarly, a Vice President of Finance falling victim to a spear-phishing social engineering attack and executing a wire transfer would result in a markedly different outcome compared to an intern in the same scenario.
Your organization can fine-tune the amplification factor of user actions by calibrating the following:
- Baseline Role Criticality (RC): Assign baseline risk levels to organizational roles based on their authority and influence.
- Access Privilege Growth Factor (): Determine how quickly risk escalates with increasing access privileges.
- Permission Values: Assign specific risk-weighted values to various permissions, reflecting their potential to cause harm if misused.
These adjustments allow the RPF model to align with your organization’s unique risk appetite and tolerance. Below, we provide illustrative values to demonstrate how you can construct an Access Privilege (AP) table to calculate the RPF effectively.
Here is a table of access privilege scoring that assigns a risk score to different types of permissions based on the potential damage they could cause if abused. The scoring considers the criticality of the system or data being accessed and the level of access granted.
Scoring Guidelines
Low Scores (1–5):
Assigned to basic or limited access with minimal potential for harm. Examples include read-only access to non-sensitive systems.Moderate Scores (6–15):
Reflect access to sensitive data, ability to modify important systems, or limited administrative privileges. These permissions could cause harm if misused but are not catastrophic.High Scores (16–25):
Represent significant administrative or critical system privileges that could disrupt core operations or lead to large-scale breaches.Extreme Scores (26–30+):
Assigned to superuser privileges or access to highly critical systems (e.g., root access, production systems). Misuse would cause catastrophic business impact.
Access Privilege Scoring
| Category | Type of Permission | Description | Suggested Score | Comments |
|---|---|---|---|---|
| Basic Access | Read-only access to non-critical systems | Access to view non-sensitive data or use basic applications (e.g., HR tools, task management). | 1 | Minimal potential for damage; typical for most employees. |
| Read/write access to non-critical systems | Ability to modify data in non-critical systems (e.g., internal blogs, file-sharing systems). | 3 | Slightly higher risk due to modification rights. | |
| Access to public-facing systems | Permissions to manage public content (e.g., website updates). | 5 | Risk depends on the system’s visibility and exposure to external threats. | |
| Sensitive Data Access | Read-only access to sensitive data | Access to view sensitive data, such as customer PII or internal financial reports. | 7 | Moderate risk due to exposure of sensitive information. |
| Read/write access to sensitive data | Ability to modify sensitive data (e.g., payroll systems, customer records). | 10 | High risk; potential for data breaches or fraud. | |
| Access to encrypted data without keys | View encrypted data but no decryption ability (e.g., backup files). | 5 | Risk is mitigated by encryption; moderate due to metadata or context exposure. | |
| Admin Access | System administrator for non-critical systems | Full control over non-critical systems (e.g., internal wikis, inventory databases). | 10 | Elevated risk; misuse can disrupt workflows or expose limited internal data. |
| Database administrator for critical systems | Full control over sensitive databases (e.g., financial or customer databases). | 15 | High risk; potential for large-scale breaches or data manipulation. | |
| Network administrator | Full control over network configurations and devices. | 20 | Significant risk; misuse can lead to widespread outages or unauthorized network activity. | |
| Access to backup and recovery systems | Ability to modify or delete backup files. | 12 | High risk; compromises recovery capabilities during an incident. | |
| Cloud administrator access | Full control over cloud resources (e.g., AWS, Azure, GCP admin roles). | 25 | Very high risk; misuse can impact infrastructure, data, and services globally. | |
| Critical System Access | Root/admin access to servers | Superuser permissions to manage critical servers (e.g., production servers, core databases). | 30 | Extreme risk due to potential for large-scale disruption or data loss. |
| Access to production systems | Privileges to deploy or modify production systems. | 20 | High risk; critical to maintaining business operations. | |
| Privileged access to OT/ICS systems | Access to operational technology or industrial control systems (e.g., SCADA systems). | 25 | High risk; misuse can disrupt critical infrastructure or safety systems. | |
| Security and Audit | Access to security tools | Permissions to view security logs and alerts. | 8 | Moderate risk; misuse can obfuscate threats. |
| Privileges to manage security configurations | Ability to modify firewall rules, IDS/IPS settings, etc. | 20 | Very high risk; can disable security protections. | |
| Access to privileged audit logs | Permissions to view or delete privileged user activity logs. | 15 | High risk; misuse can erase evidence of malicious actions. | |
| Financial and Legal | Access to financial systems | Permissions to approve payments or manage accounts (e.g., ERP systems, payroll). | 15 | High risk; direct potential for financial fraud. |
| Access to compliance or legal data | Permissions to view regulatory or legal data (e.g., GDPR or litigation documents). | 10 | Moderate risk; potential for compliance violations or sensitive data exposure. | |
| User Management | Privileges to manage user accounts | Permissions to add, modify, or delete user accounts. | 12 | High risk; misuse can grant unauthorized access or create shadow accounts. |
| Privileges to assign roles and privileges | Ability to assign permissions or roles to others. | 15 | High risk; misuse can escalate access and compromise segregation of duties. | |
| Access to identity federation systems | Permissions to manage SSO or identity providers (e.g., Okta, Azure AD). | 20 | Significant risk; misuse can compromise organization-wide access. | |
| Data Transfers | Access to data export tools | Permissions to extract data from systems (e.g., via APIs or bulk downloads). | 12 | High risk; facilitates data exfiltration. |
| Privileges to transfer data externally | Ability to upload data to external systems (e.g., FTP, cloud storage). | 15 | High risk; potential for data leaks or exfiltration. | |
| Physical Access | Privileges to access restricted areas | Physical access to data centers or secure rooms. | 8 | Moderate risk; could lead to physical tampering or theft. |
| Privileges to manage physical access systems | Ability to modify badge access or physical security controls. | 12 | High risk; misuse could allow unauthorized physical entry. |
Finally, here’s a suggested table of baseline Role Criticality (RC) values across various business functions, reflecting the potential impact of actions taken by roles within those functions. These baseline RC values range from 0 (low impact) to 1 (highest impact), aligning with their authority, influence, and potential to amplify risk if compromised.
Below provides a possible mapping of baseline values to roles within your organization, with some explanatory commentary.
Key Observations
Incremental RC Levels by Role:
- Junior roles (e.g., interns, assistants) have low RC values, reflecting their limited influence and access.
- Mid-level roles (e.g., managers, analysts) have moderate RC values, as their decisions or actions impact specific areas but are less likely to cause widespread harm.
- Senior roles (e.g., VP, C-suite) have high RC values due to their organizational authority and broader influence.
Function-Specific Variations:
- Finance and Security roles tend to have higher RC values compared to functions like HR or Sales, as misuse in these areas often carries greater financial or operational consequences.
- Engineering and IT roles may have higher RC values for mid-level roles (e.g., administrators, developers) due to their access to critical systems and repositories.
Custom Calibration:
- These RC values can be adjusted to align with your organization’s unique structure, priorities, and risk appetite.
Baseline Role Criticality (RC) Across Business Functions
| Function | Role | Suggested RC | Comments |
|---|---|---|---|
| IT | Intern | 0.1 | Limited authority; minimal role in decision-making or systems management. |
| System Administrator | 0.6 | Moderate authority over systems and configurations; potential to disrupt operations. | |
| Network Administrator | 0.7 | High influence over network security and availability; misuse could cause widespread disruptions. | |
| Chief Information Officer (CIO) | 0.8 | Strategic role with influence over IT policies; compromise impacts the organization significantly. | |
| Engineering | Junior Engineer | 0.2 | Limited authority; access often restricted to non-critical systems. |
| Software Developer | 0.4 | Moderate access to codebases; potential for vulnerabilities or backdoor introduction. | |
| Engineering Manager | 0.5 | Authority over teams and projects; higher access to critical systems or repositories. | |
| Chief Technology Officer (CTO) | 0.8 | Strategic role; decisions can impact product direction, security, and architecture. | |
| Finance | Accounts Payable Clerk | 0.4 | Moderate access to financial systems; potential for fraudulent transactions. |
| Financial Analyst | 0.5 | Access to sensitive financial data; misuse could lead to data leaks or mismanagement. | |
| VP of Finance | 0.7 | High authority over financial operations; critical decisions and approvals could be compromised. | |
| Chief Financial Officer (CFO) | 0.9 | Strategic role overseeing all financial operations; compromise could lead to catastrophic losses. | |
| Security | Security Analyst | 0.5 | Moderate authority; access to threat intelligence and monitoring systems. |
| Security Architect | 0.6 | Influence over security designs and controls; misuse can introduce vulnerabilities. | |
| Chief Information Security Officer (CISO) | 0.9 | Strategic security role; responsible for overall organizational security posture. | |
| HR | HR Assistant | 0.2 | Limited access to sensitive data; actions unlikely to have a widespread impact. |
| HR Manager | 0.4 | Access to sensitive employee data; potential for compliance and privacy risks. | |
| Director of HR | 0.6 | High authority over personnel decisions and systems; misuse could impact workforce and compliance. | |
| Sales | Sales Representative | 0.3 | Limited access to sensitive data; risk lies in customer relationships and deals. |
| Sales Manager | 0.5 | Authority over deals and team performance; misuse could affect client relationships or revenue. | |
| VP of Sales | 0.7 | High authority over revenue generation; strategic role impacts growth and market presence. | |
| Executive | Chief Executive Officer (CEO) | 1.0 | Highest authority; decisions impact the entire organization. |
| Chief Operating Officer (COO) | 0.9 | High influence over operational strategies; critical for business continuity. | |
| Board Member | 0.8 | Strategic oversight role; influence over governance and decision-making. |
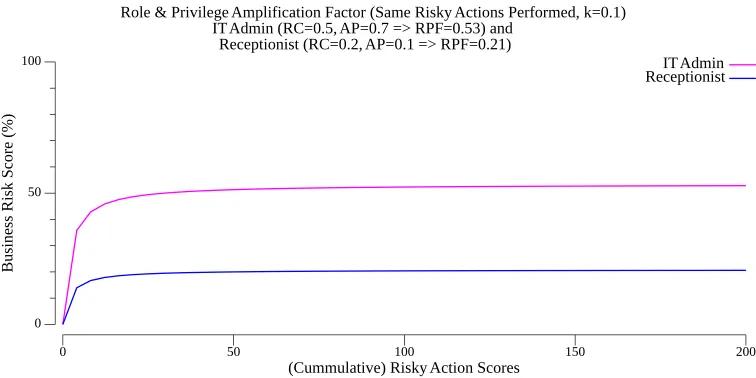
To see the impact of the Role & Privilege Amplification factor on the business risk score. Consider two employees, an IT Admin and a Receptionist who performed the exact same risky actions. The curve below shows the RPF effect on the evolution of their risk scores.
Taking Action with Continuous Human Risk Intelligence
Our goal is to use the Continuous Human Risk Intelligence framework defined above to manage Human Risk and to support decision-making to drive continuous improvements in our organizations risk exposure. Here are some ideas.
To demonstrate the Business Risk Score (BRS) in action for decision-making and continuous human risk management, let us explore a few scenarios. These scenarios help identify risks, analyze trends, and take corrective actions based on insights from the model.
Use Cases for BRS in Decision-Making
1. Privilege Clawback Initiative
- Objective: Identify users with excessive access privileges and reduce them to mitigate risk.
- Example:
- Calculate BRS for all users and observe how Access Privileges (AP) contribute to high scores.
- Highlight cases where AP growth drives risk escalation disproportionately, especially for roles like IT admins or engineers.
- Action:
- Initiate a privilege review process for users with high BRS driven by excessive AP.
- Implement least-privilege principles and revoke unused or excessive permissions.
2. Behavioral Risk Mitigation
- Objective: Track trends in click-through rates on phishing links and reduce them through training or simulation campaigns.
- Example:
- Observe how users’ BRS evolves over time as they engage in risky behaviors like clicking phishing links.
- Compare the effectiveness of awareness training by tracking improvements in HRS ( increases, decreases).
- Action:
- Focus training on users or groups whose BRS shows limited improvement despite previous initiatives.
- Create targeted simulations to reduce risky behaviors.
3. Misconfiguration and Environmental Risk Monitoring
- Objective: Detect trends in system misconfigurations or vulnerabilities that increase Environmental Risk (E).
- Example:
- Analyze spikes in BRS across departments caused by bad environmental actions (), such as disabling antivirus or failing to patch systems.
- Identify high-risk teams (e.g., engineering or IT) for targeted interventions.
- Action:
- Automate alerts for misconfigurations that push BRS beyond acceptable thresholds.
- Schedule compliance audits or enforce automated fixes for critical misconfigurations.
4. Advanced Human Risk Quantification with Monte Carlo Simulation
Objective:
Simulate and quantify the potential risk impact of employees, contractors, and partners to gain a deeper understanding of your organization’s human risk exposure. This analysis enables strategic initiatives to reduce risk, optimize interventions, and allocate resources effectively.Approach:
Use Monte Carlo simulations to model the distribution of potential outcomes based on user actions, role criticality, and access privileges. The simulation incorporates probabilities of different risk events (e.g., phishing clicks, privilege misuse, misconfigurations) and their business impacts.Steps:
Define Input Variables:
- Human Risk Score (HRS): Use Bayesian-updated HRS values for each user, reflecting their observed behaviors and environmental factors.
- Role & Privilege Factor (RPF): Combine role criticality (RC) and access privileges (AP) to determine potential impact amplification.
- Risk Event Probabilities: Assign probabilities to specific risk events (e.g., phishing click rate = 5%, misconfiguration rate = 10%). You have this data from and .
- Business Impact per Event: Estimate financial or operational impacts for each event type (e.g., phishing attack = $50k, misconfiguration = $100k).
Run Simulations:
- Generate random user actions and event occurrences based on predefined probabilities.
- Calculate the total organizational risk impact by summing the simulated outcomes for all users and roles.
- Repeat the simulation thousands of times to produce a distribution of potential outcomes.
Analyze Results:
- Exceedance Curves: Plot the probability of exceeding specific risk thresholds (e.g., 10% chance of exceeding $1M in losses).
- Risk Concentration: Identify roles or groups contributing disproportionately to risk (e.g., IT Admins, Finance VPs).
- Scenario Comparisons: Simulate changes in risk under different scenarios, such as reducing permissions, increasing training, or implementing MFA.
Actionable Insights:
- Privilege Optimization: Identify high-risk users with excessive permissions and prioritize a privilege clawback initiative.
- Training Effectiveness: Quantify how improvements in HRS (e.g., fewer phishing clicks) reduce overall risk exposure.
- Strategic Interventions: Allocate resources to roles or departments contributing most to organizational risk.
Visualization:
- Exceedance Curve: Show the likelihood of losses exceeding specific thresholds under current conditions.
- Heatmap: Display risk contributions by department or role.
- What-If Scenarios: Compare organizational risk before and after implementing privilege reductions or awareness campaigns.
Additional Considerations
Human risk in cybersecurity emerges at the intersection of people, privileges, and technology. It’s not just about individual actions - it’s about how these actions interact with systems and access rights to create potential risk scenarios. Whether it’s an employee falling for a phishing attack, a contractor misconfiguring critical systems, or an insider abusing privileges, the risk equation always involves multiple components.
This multi-dimensional nature suggests multiple key intervention points:
Human Behavior Management
- Continuous adaptive feedback loops
- Context-aware security training
- AI-powered risk co-pilots for decision support
- Real-time behavioral analytics and coaching
Access Control Intelligence
- Dynamic least-privilege enforcement
- Risk-based conditional access
- Just-in-time privilege elevation
- Continuous access right optimization
Technical Environment Hardening
- Zero trust architecture implementation
- System posture monitoring and enhancement
- Automated security controls
- Resilient system design
Deterrence and Detection Framework
- User activity monitoring and analytics
- Behavioral anomaly detection
- Clear policies on consequences of malicious actions
- Digital forensics capabilities
- Insider threat monitoring programs
- Regular security audits and investigations
By integrating deterrence with our other control measures, organizations create a comprehensive framework that not only prevents accidental incidents but also discourages and detects intentional malicious behavior.
Conclusion
The Business Risk Score (BRS) provides a powerful, data-driven approach to quantifying and managing human-centric risks within an organization. By integrating Human Risk Score (HRS), reflecting individual behaviors and environmental influences, with the Role & Privilege Factor (RPF), which captures the amplification of risk due to access privileges and role criticality, the BRS offers a comprehensive view of organizational vulnerability.
Through practical applications, such as tracking privilege growth to drive clawback initiatives, analyzing trends in user behavior to target training, and leveraging Monte Carlo simulations to quantify and visualize risk exposure, the BRS enables informed, proactive decision-making.
This framework not only equips organizations to address immediate threats but also establishes a foundation for continuous risk intelligence. It aligns mitigation strategies with business priorities, helping leaders balance operational efficiency with security imperatives. As cybersecurity risks evolve, adopting dynamic, adaptive tools like the BRS ensures organizations remain resilient and well-prepared to manage the human elements of risk effectively.